Lurk Under Wires
You are an enigmatic hacker, or possibly a malevolent AI, lurking somewhere on the world. See the @ symbol on the world map? That’s you.
Your enemies are elsewhere on the world map – you don’t know where. Your task is to send out Objects throughout the Internet to seek them down and destroy them. Your enemies are seeking to do the same to you, and also to each other.
Downloads:
Windows
Linux build, may or may not work.
Source – also available at http://hub.darcs.net/PTSnoop/7DRL_2013 .
Controls:
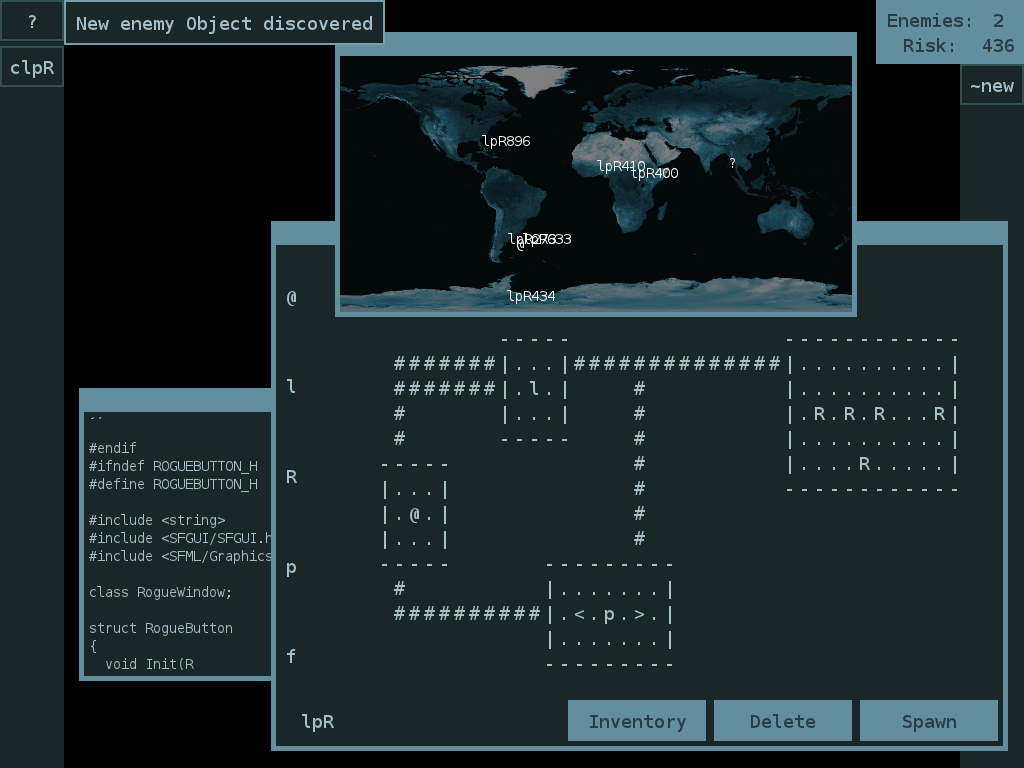
The game mostly takes place in three windows, which I’m calling the “World”, “Rogue”, and “Mash” windows. The World map shows where in the world your Objects are, and also any enemy Objects or enemy bases that you’ve discovered.
The Mash window is your way of progressing the game – when the Mash window is open, each time you press a key on your keyboard, the game moves forward one turn. The best way to move rapidly forward in time is to mash your keyboard like you’re a hacker in a movie. Press the spacebar to show or hide the Mash window.
Objects – your computational minions throughout the world – are created and represented as ASCII pictures of traditional Roguelike dungeons. You can create these dungeons in the Rogue window. Press the “~new” button on the bar to the right of your screen to open this window.
The Rogue window gives you some letters (room types) on the left hand side, and a big empty space to draw in. To draw a dungeon, click on a room type, then click somewhere in the big empty space. The room and some corridors will be automatically filled in. There’ll be more information on the room types later on. Each dungeon must have one “@” room – you won’t be able to place any other rooms until you’ve got one.
Once you’re happy with your dungeon, you can press the “Spawn” button to send one of those Objects forth into the world to do your bidding. You can also use the “Inventory” button to store the dungeon on the bar to your right – you can spawn new copies by clicking on the newly-created button. Or you can press the “Delete” button to discard the dungeon and close the Rogue window.
In the top right corner of the screen, you’ll see how many of your enemies are still alive, and your current risk of discovery. Creating Objects increases this Risk. Objects with lots of rooms will increase your Risk substantially more, so use your rooms efficiently if you want to stay undetected.
Press the Escape key to quit the game.
Rooms:
There are ten different types of rooms available in Lurk Under Wires. At the start of the game, you can place @Playerbase, Look, forage, Rock, and Ping rooms.
@Playerbase
– this allows the Object to function. All Objects must have one of these.
Look
– This room will seek through the world, trying to find enemy Objects. Without a Look room, an Object will only ever know about the enemies that the player knew about when it was spawned.
forage
– This room will forage through the datastreams of the world, trying to discover new types of room for you to use. If you never place any of these, you’ll never access any of the higher-end rooms.
Rock
BPaper
XScissors
– These rooms will attempt to attack any enemies that the Object knows about. Rock is weak against BPaper, which is weak against XScissors but strong against Rock, as you’d expect. Rock is the only attack type available at the beginning of the game.
Ping
– This room will send signals back to your base, so you learn what the Object is doing. If an enemy Object is discovered, this room will give you its coordinates, and any subsequent rooms you spawn will also know about the enemy Object (and be able to attack it). Also, pings let you know that an object is still alive. However, too many pings can make you vulnerable to late-game Snoop attacks.
Friendping
– This room will send signals to all the other friendly Objects if any enemy Objects are discovered, without sending signals back to the player.
Snoop
– This room will sit patiently and listen for Ping traffic. If it hears a Ping, it has a chance of tracing its source or its destination. If a player has a lot of Pinging Objects, this can be very dangerous for their base, which will be recieving a lot of traffic.
Decoy
– This doesn’t do much.